Posted on
January 10, 2019
Updated on
March 20, 2024
Read time
 9 mins read
9 mins read
Regardless of who you are – an owner of a small humble blog, an e-commerce store selling dog food or a corporate juggernaut web solution, getting your website or web application hacked is the scariest thing that can ever happen.
But the truth is – your website can be hacked if you are careless about its security.
The flaws and loopholes in the website also known as web vulnerabilities give hackers a backdoor to sneak into your website. And once they manage to get in, the consequences are dire.
They can steal the important business or user information, access the admin panel, post something that damages your goodwill, alter the database or in worst case delete it.
In the year 2018, the world witnessed asserted incidents of the web security breach that left everyone wide-eyed. Some of the popular ones (or maybe unpopular) being the industry juggernauts like Facebook, Google+ and British Airways that compromised the user’s data to the hackers.
When it comes to small business, the scenario is even worst. A report by security firm Sitelock reveals that average small business websites are attacked 44 times a day and software “bots” visit these sites on average of 152 million times a week.
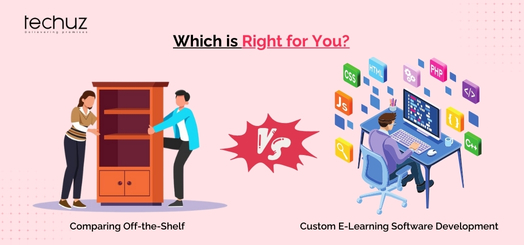
Further, just to spotlight the amount of damage cybercrime is expected to do to business is a gargantuan $6 billion! This annual loss is more than the GDP of Canada, Saudi Arabia, Australia and Switzerland combined!
All these sinister stats alludes one thing – if you haven’t worked on your web security yet, it’s the time now. As a web development company, we take utmost care for the security of our web applications. So here, we have made a list of five common security threats and vulnerabilities that websites and web apps typically face and how you can prevent them.
1. SQL Injection
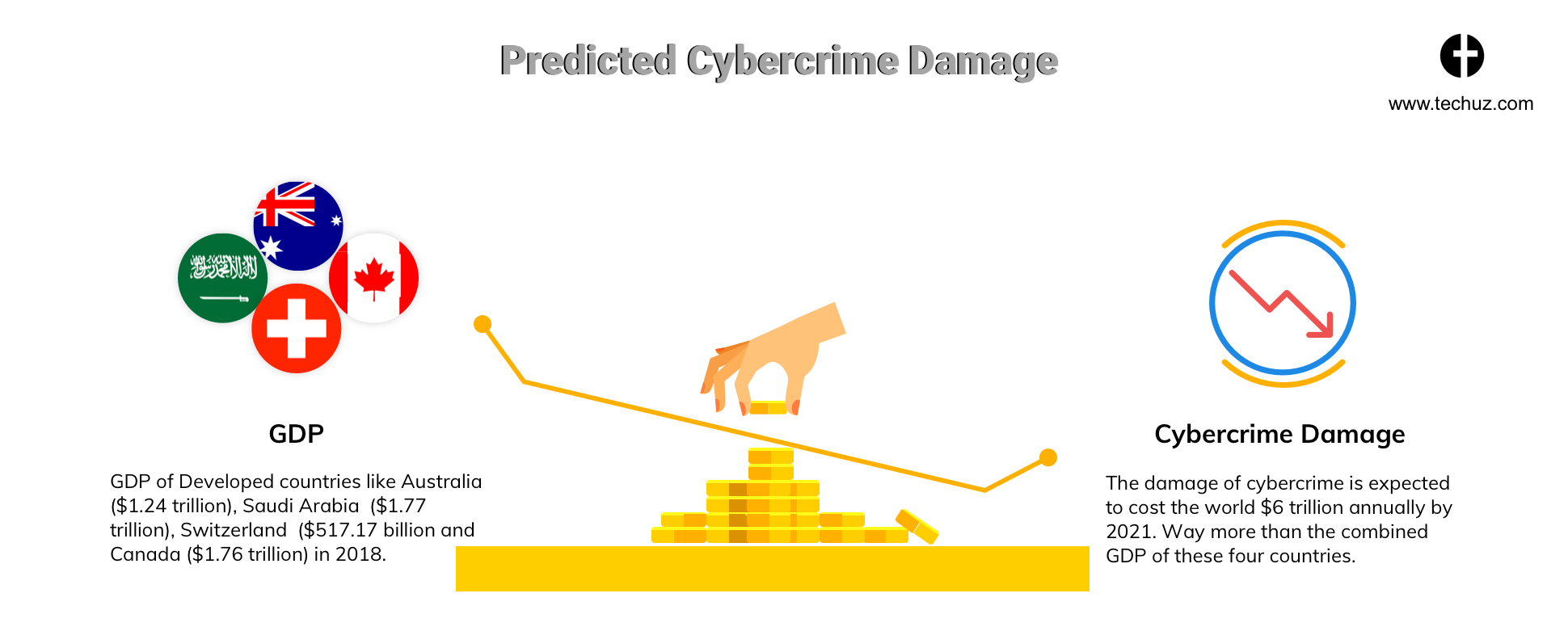
SQL injection is one of the most common ways of hacking websites and web application. In this, the attacker injects and executes a malicious SQL code that provides him the access of the web application’s database.
Sidenote: Just in case you are unaware of SQL – it is a command-and-control language for traditional/relational databases such as MySQL, PostgreSQL, Oracle and MariaDB. Most of the web applications and websites are built using PHP, ASP.NET and other scripting languages that use these SQL databases. This also makes it one of the most common and widely used technique to hack web apps and websites.
So, once the hackers have found the hole in the armor, i.e. SQL injection vulnerability, they can do massive damage to your web app.
Since SQL’s function is to fetch the data for the query and display the result an SQL injection can disclose entire data from the database.
Not only that, the attacker can even make changes to the actual data.
As mentioned previously, the worst part could be deleting the entire database. Moreover, even if the data has been backed up properly, it could temporarily interrupt the application until everything is restored.
How to prevent/mitigate SQL injection?
Sanitizing and validation
Sanitizing and validation are used to check the user input and prevent any kind of malicious injection. They are considered to be the best coding practice for the security of the web application.
Update and patch management
Hackers discover new vulnerabilities to inject malicious SQL codes. Thus, it is quintessential to update the software and patches.
Using a web application firewall
Web application firewall filters out the malicious data and codes keeping the application safe. It runs on a set of rules that can be changed and updated when necessary.
2. Broken authentication and session management
Authentication is an integral part of any web application. Most of the web app we use today have some sort of authentication mechanism. Its purpose is to verify the user’s identity and grant or deny the access and privileges of the application.
However, if there is any flaw in it, the hacker can bypass the authentication and breach the security. Generally, this type of attacks occurs due to improper implementation of authentication and session management such as:
- Poor or predictable login credentials
- Authentication credentials are not secured (unencrypted) when stored
- Credentials such as passwords and session IDs being sent over unencrypted connections
- No session timeout
- Validating the session value even after logout
How to prevent it from hackers?
Password length and complexity
It’s quite a common practice these days to have a password with alphanumeric characters consisting of letters, numbers, symbols, and punctuations. Also, the recommended minimum length of the password is set to be at least eight characters. All this complexity makes the password harder to guess.
Brute force attack protection
A brute force attack is used by hackers to crack the passwords by the trial-and-error method. Thus, in order to prevent those type of attacks, the accounts are disabled temporarily on a number of invalid login attempts.
Encryption of credentials
The authentication credentials such as passwords and session IDs should be properly encrypted when stored. Also, the credential must not be sent over unencrypted connections.
3. DNS cache poisoning
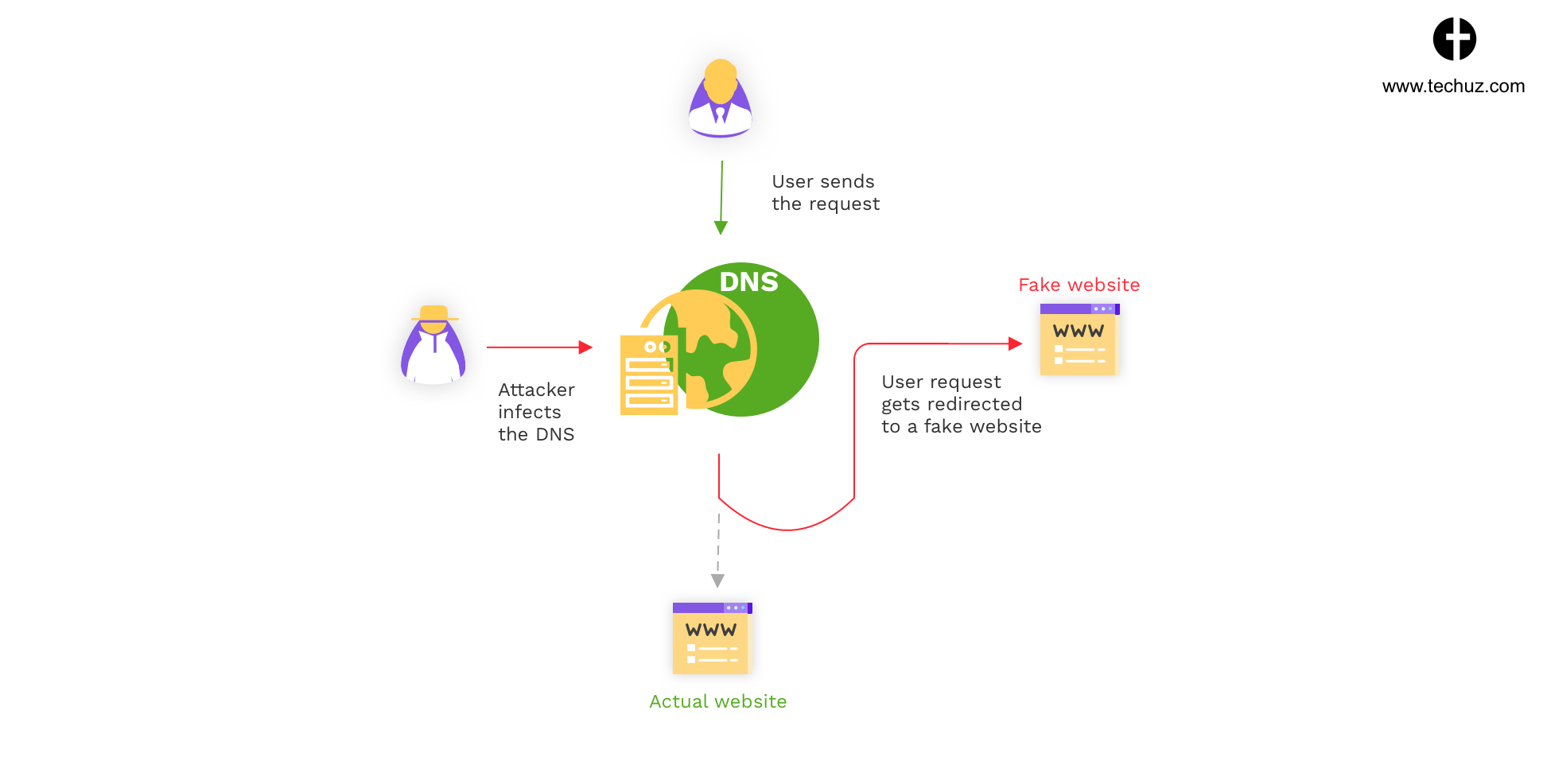
Domain Name System is something that keeps the register of domain names and converts them to computer-readable IP (Internet Protocol) addresses. Whenever a user enters a domain name (e.g. xyz.com) in the browser, it first contacts the DNS server which in return responds with one or more IP address to reach xyz.com. Thus, now the computer can connect to the computer-readable numeric IP address.
DNS (Domain Name Server) cache poisoning also known as DNS spoofing, is an attack on the domain name system. Here, the hacker exploits the vulnerabilities in the DNS to redirect the users from the actual servers to the fake ones controlled by them.
To put in other words, your users would be entering the right domain name but are directed to a wrong IP address.
How to prevent DNS cache poisoning?
DNSSEC
DNSSEC (Domain Name System Security Extension) is one of the most widely used tools to prevent DNS poisoning. Once DNSSEC is deployed, it helps to recognize and confirm if the DNS responses are authentic or not.
Educate the user
The users must be educated on identifying malicious sites and phishing emails.
Keeping the DNS up to date
Outdated DNS servers are more prone to vulnerabilities so it is essential to keep them up-to-date. The latest versions of the DNS servers comes with updated security patches that fortify the server’s security.
4. DDoS – Distributed Denial of Services
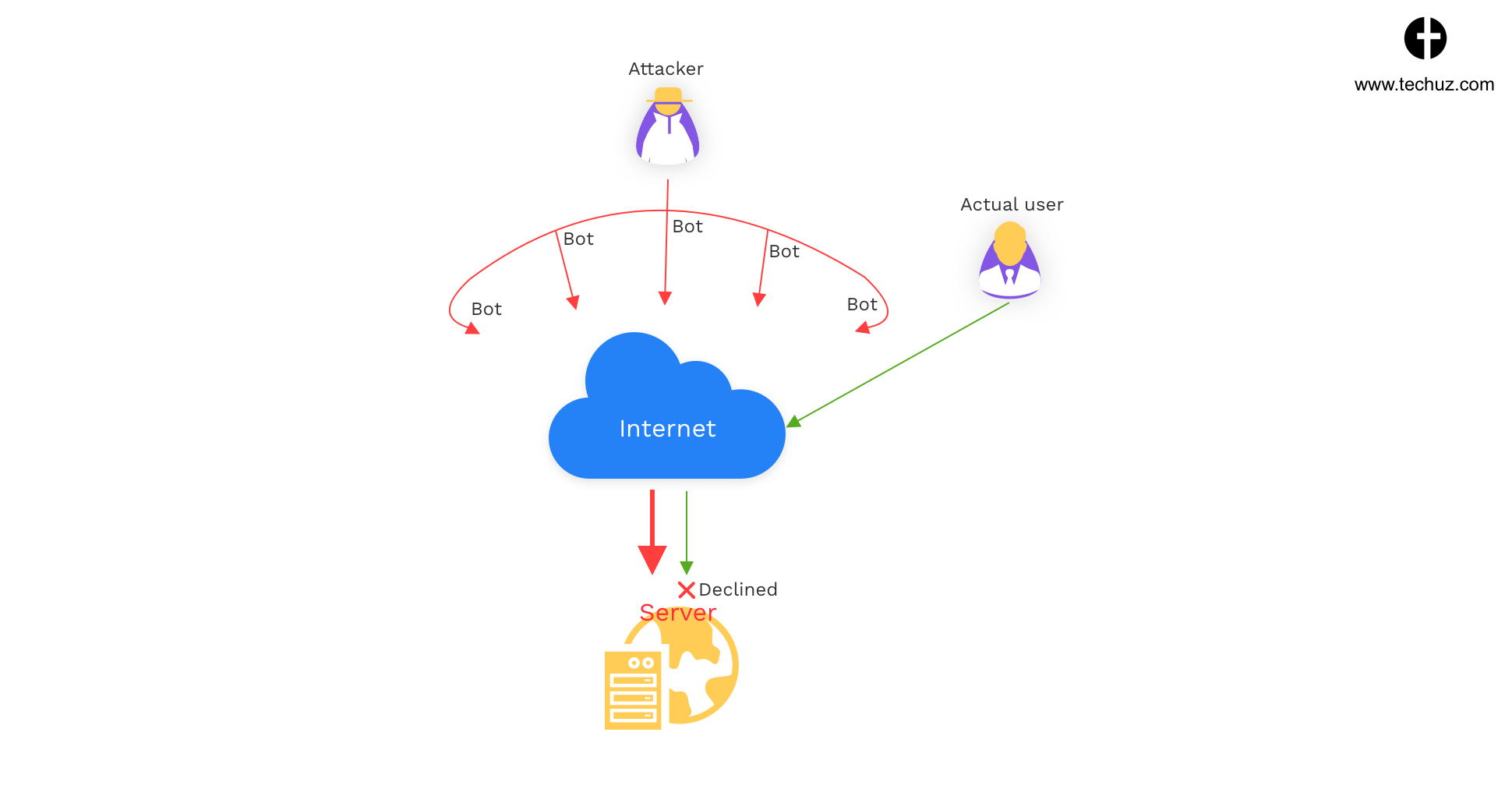
DDoS is a malicious attack to disrupt the normal working of the web app or website by overwhelming the server with a flood of unnecessary traffic. This overload results in a kind of traffic jam that affects the application and prevents its functionality.
DDoS attacks are different from DoS (Denial of Service). DoS attacks are performed from typically one computer/network whereas in DDoS the attacker uses multiple compromised systems and networks that makes it more difficult to hamper the attack.
No doubt, these attacks have dire consequences on business. As per a report, DDoS attacks can cost a huge enterprise as much as $40,000 per hour and a massive decline in customer trust by 43%.
How to prevent/mitigate DDoS?
Understanding the signs
In order to prevent or mitigate the attack, it is essential to understand its warning signs. Some of the signs include – network slowdown, occasional unexplained shutdowns or a sudden spike in traffic. Even being able to differentiate between the attack and normal traffic, for instance – a surge in traffic during festive offers for an e-commerce store vs overwhelming traffic for no reason.
Using a CDN
Content Delivery Networks (CDN) are servers distributed at different geographical locations where information is cached from the origin server. These distributed servers also known as PoPs helps to reduce the latency and deliver a faster browsing experience. These servers also help in mitigating the attack intensity by absorbing it across the different geographical locations, which without CDN, could shut down the sole origin server.
Web application firewall
A web application firewall protects the server and mitigates the attack by acting as a reverse proxy. Another amazing feature of WAF is that it can filter the bad requests using the rules entered to recognize the DDoS and it does it quite quickly whenever the application is attacked.
5. Cross Site Scripting (XSS) Attacks
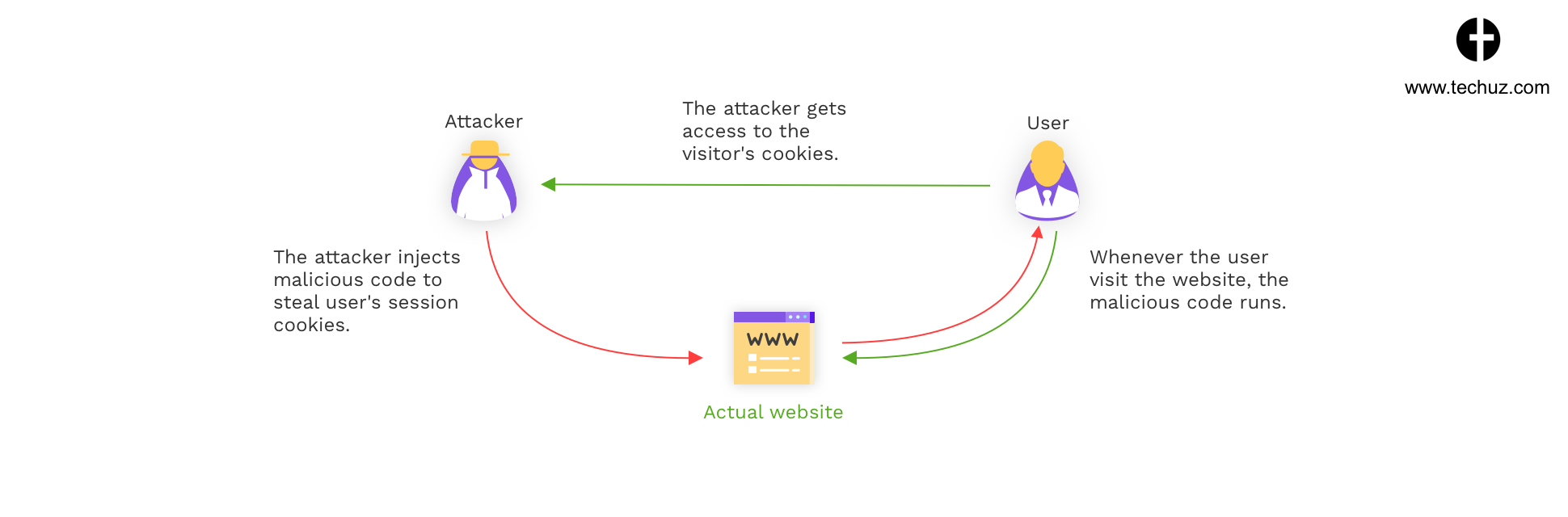
Cross Site Scripting (XSS) is another type of code injection where the hacker inserts malicious code to infect the program and get the access over it. However, unlike SQL the user of the application is at the risk instead of the web application.
When the user visits the page that contains the malicious JavaScript code, their browser gets infected. Now, once that code is executed, the hacker has access to the user’s browsing cookies that includes username, password and other data. The attacker can also activate Trojan programs, modify the page content and even control the browser remotely.
How to prevent/mitigate XSS?
Sanitize and validate user input
Since XSS is a type of code injection just like SQL, sanitizing is a must. In order to prevent the injection of any type of malicious, we must validate the user input.
Escaping
Another method that you can use to prevent XSS is escaping user input. Escaping refers censoring the disallowed characters that can damage the application or user.
Wrapping Up
Hope this post has given you an idea on some of the most popular ways websites get hacked. The whole point of the blog boils down to keeping a forward stance when it comes to the security of the website/web application. No doubt, design, user experience and performance matters a lot but we can not neglect the gravity of security. So when you develop your app or hire a web development company, ensure proper security standards and coding practices are followed and your app passes through various meticulous tests to make your product impeccable.